I recently presented a talk at Python WA about two security features that are available in software registries like PyPI (Python Package Index); trusted publishing and digital attestations and how they increase trust in the software supply chain.
Trusted Publishing is a mechanism for uploading packages that uses the OpenID Connect (OIDC) standard to exchange short-lived identity tokens between a trusted third-party service and PyPI (and other software registries) instead of long-lived API tokens.
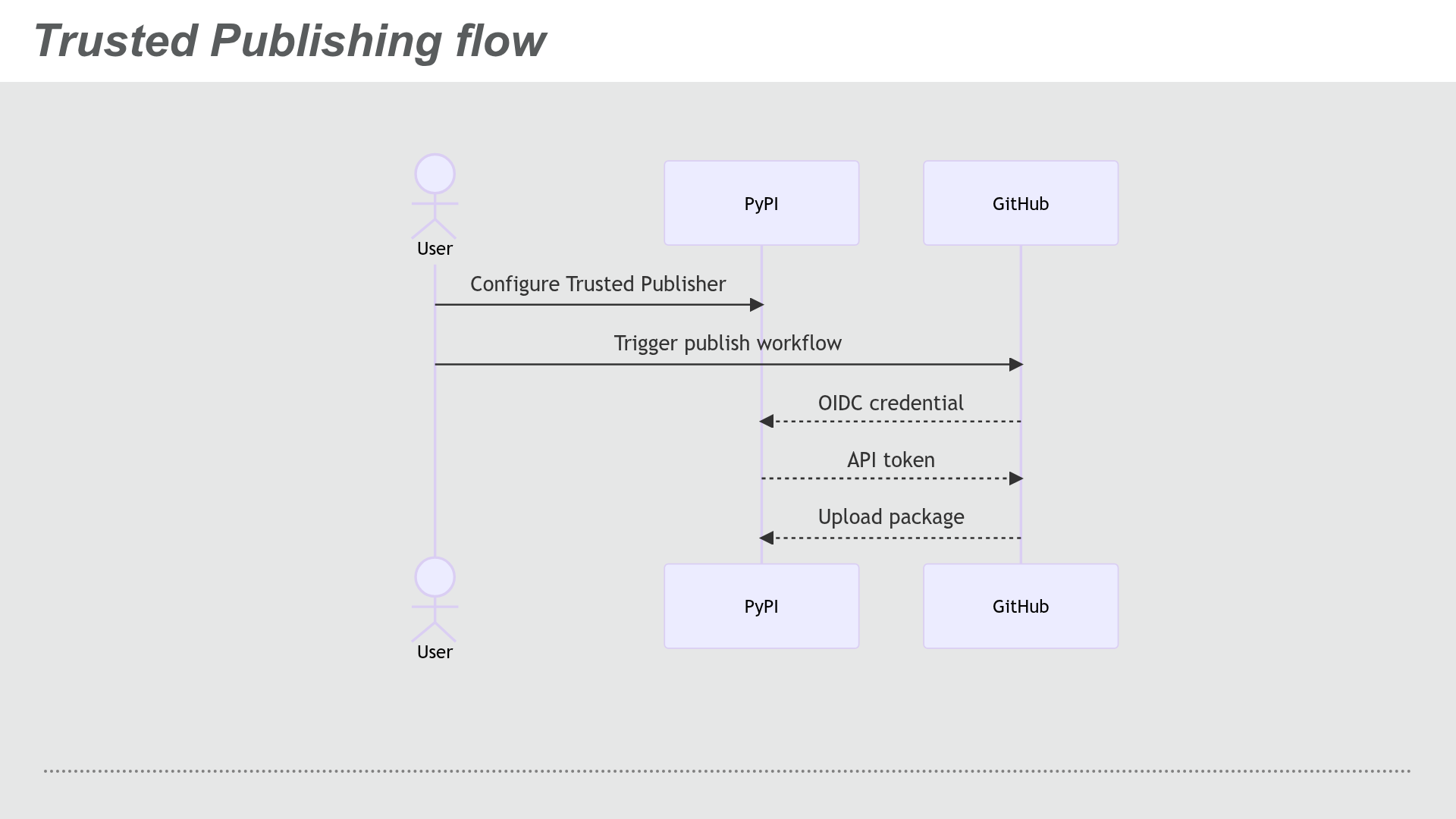
Trusted Publishing flow
Enabling a trusted publisher requires different configuration requirements based on your CI/CD platform. The following platforms are supported by PyPI:
- GitHub Actions
- GitLab CI/CD
- Google Cloud
- ActiveState
For GitHub Actions, you must provide the repository owner’s name, the repository’s name, and the filename of the GitHub Actions workflow that’s authorized to upload to PyPI. In addition, you may optionally provide the name of a GitHub Actions environment.
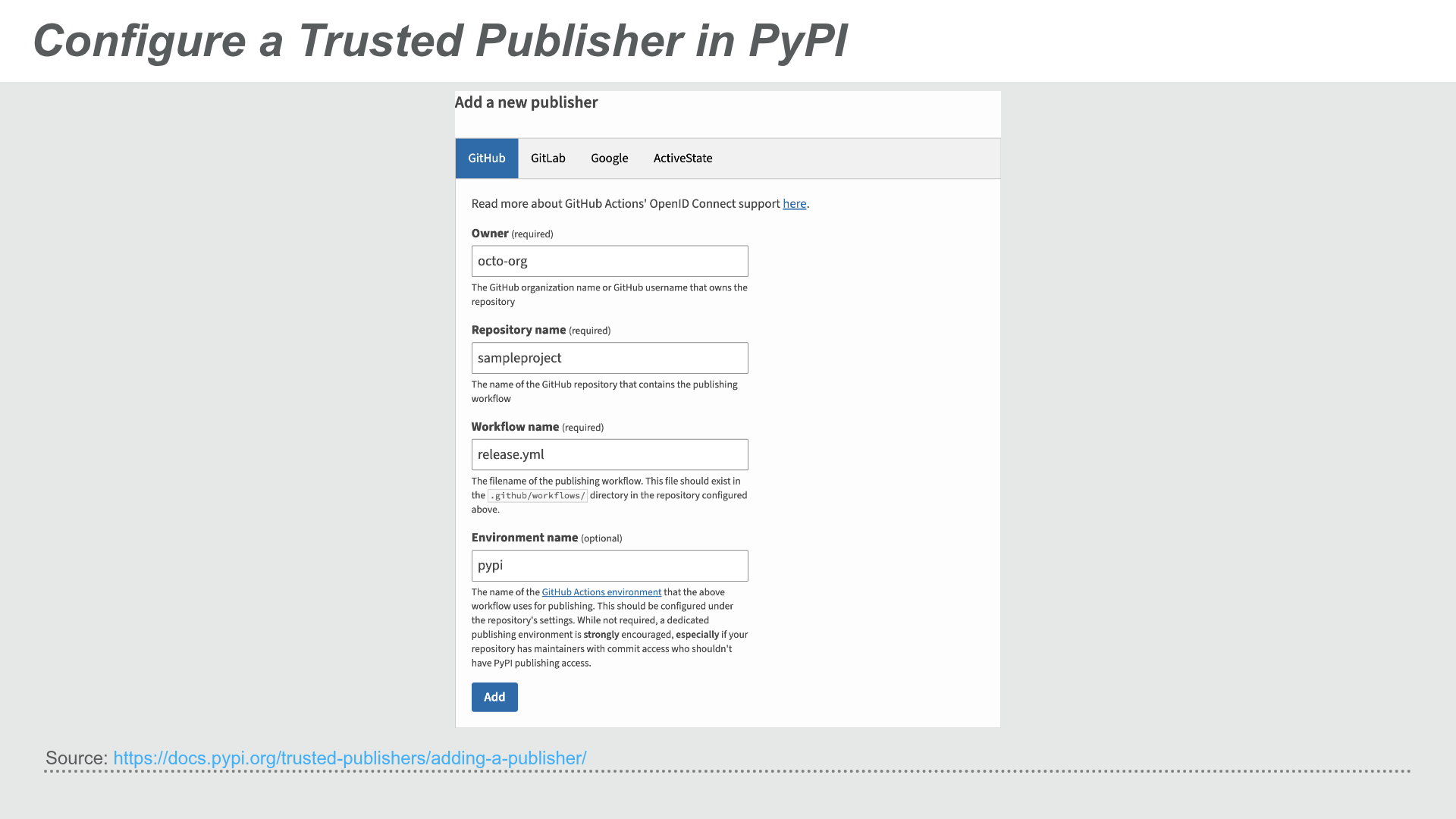
Configuring a Trusted Publisher in PyPI - screenshot showing the configuration form with fields for repository owner, repository name, workflow filename, and optional environment name
Publishing requirements will also differ depending on the platform, if you’re using GitHub Actions the blessed way is to use PyPA’s (Python Package Authority) pypi-publish action.

Trusted Publishing to PyPI Github Action
This removes the need of managing a shared secret between PyPI and the CI/CD platform that provides usability and security benefits.
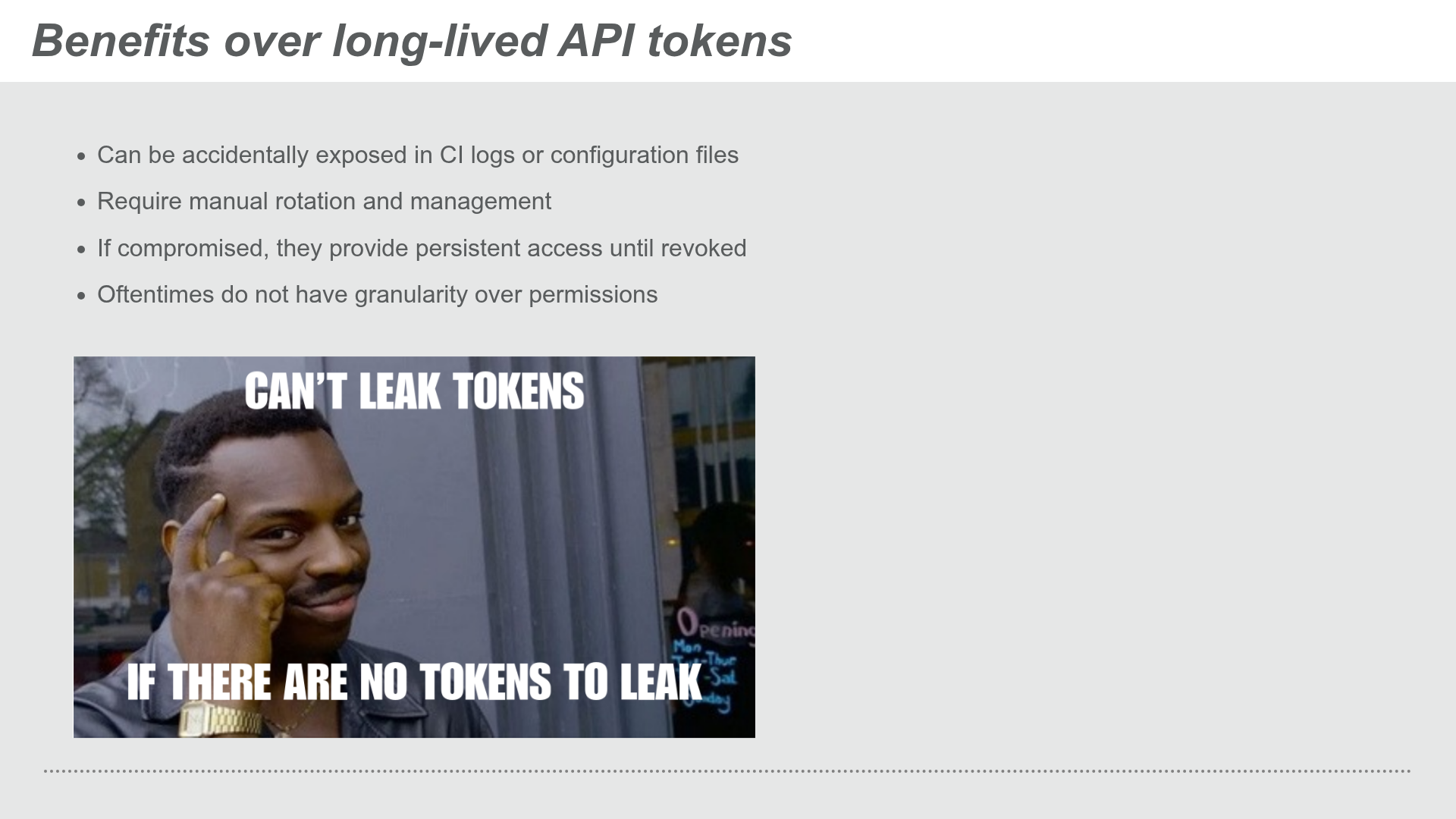
Benefits of trusted publishing vs long-lived API tokens
This is not limited to PyPI and has seen adoption across the broader open-source ecosystem with other package registries also adding support. As of this writing, the following package registries (that I know of) support Trusted Publishing:
- Ruby’s RubyGems
- Rust’s Crates
- Dart’s Pub Package Registry
- JavaScript’s npm and JSR
Trusted Publishing adoption in software registries
Trusted Publishing gives us provenance i.e. verifiable metadata that details a software artifact’s origin and unlocks attestations – which are cryptographically signed signatures that provide a verifiable link to an artifact or package’s original source location (provenance).
Support for digital attestations in PyPI was added in PEP 740. PyPI currently supports the following attestations:
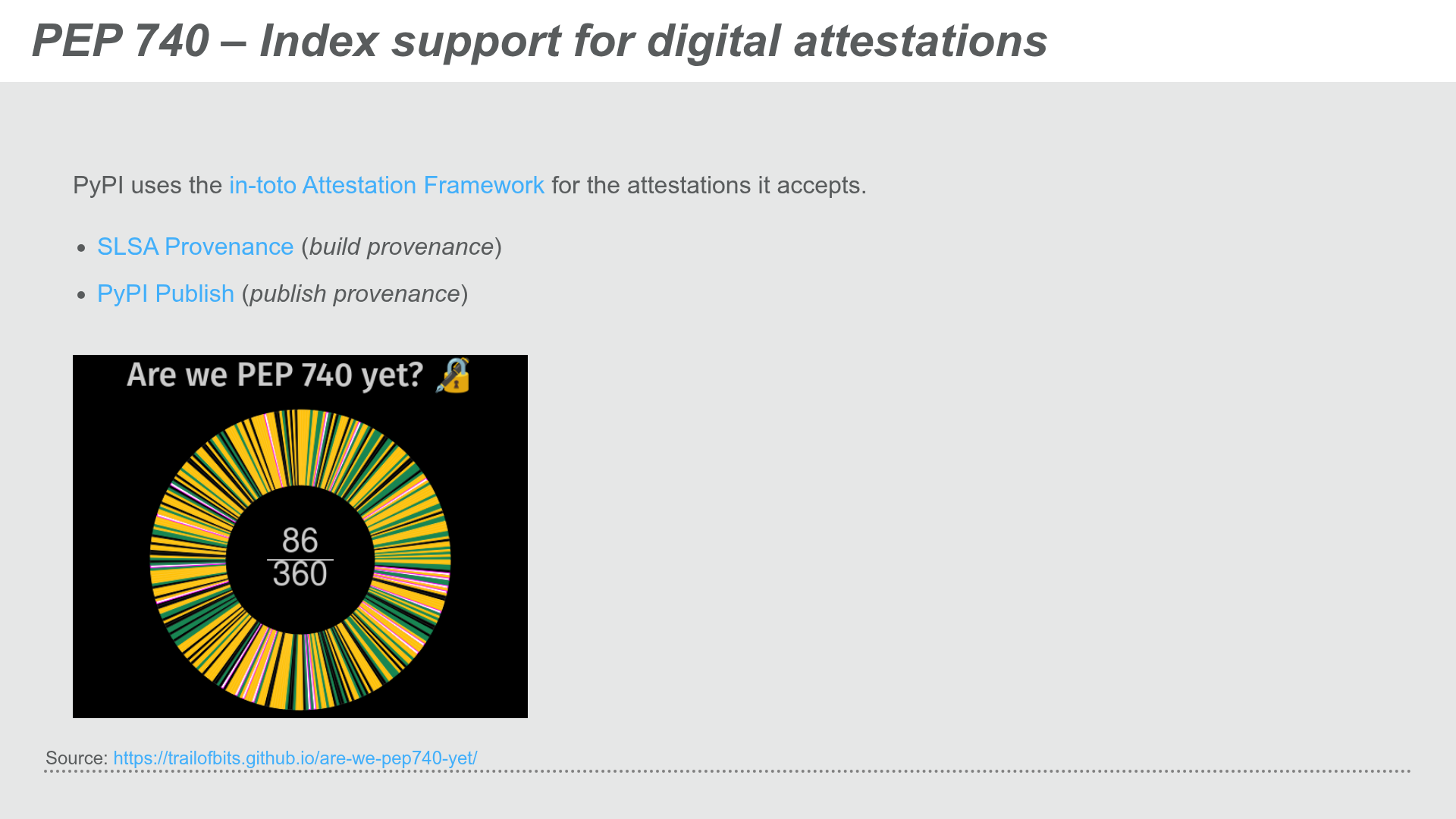
PEP 740 Index support for digital attestations
Sigstore is a set of tools that is used for digital signing, verification, and checking of package provenance.
It integrates with the Trusted Publishing process through the CI/CD platform, the latter sends the OIDC token together with a public key (from an ephemeral private + public key pair) to Fulcio which validates the token and sends back a signing certificate.
The signing certificate is then used to sign the attestations that are uploaded to Rekor which saves an immutable record to which the signatures can be verified against, the attestations are then published together with package to the target software registry.
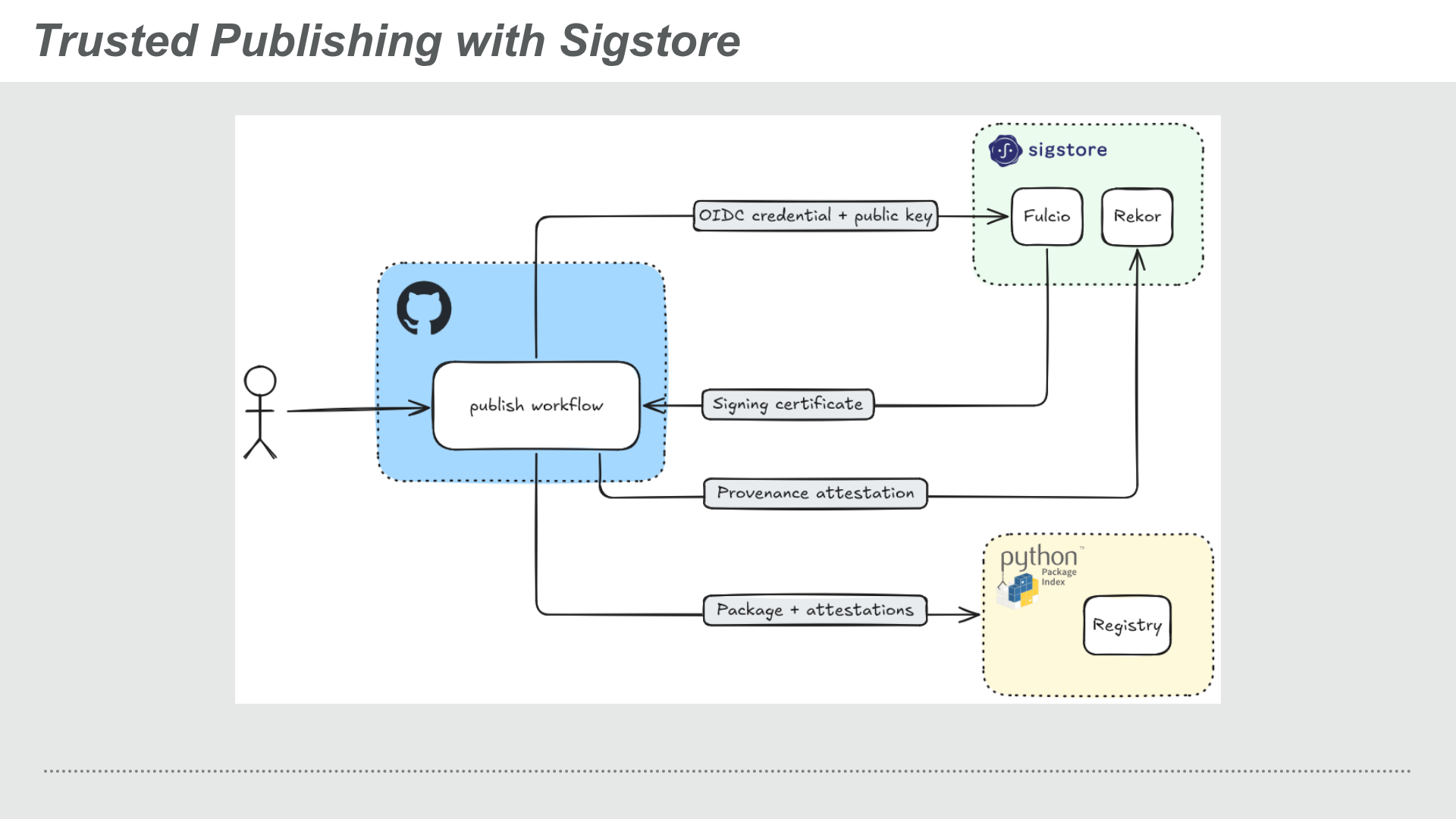
Trusted Publishing with Sigstore
PyPI supports the following platforms that can produce attestations:
- GitHub Actions
- GitLab CI/CD
- Google Cloud
If you’re using GitHub Actions and PyPA’s pypi-publish action (for version v1.11+), attestations are generated and uploaded automatically by default with no additional configuration necessary.
PyPI provides two ways of consuming attestations, one through a Provenance section in the package UI and programatically through its Integrity API.
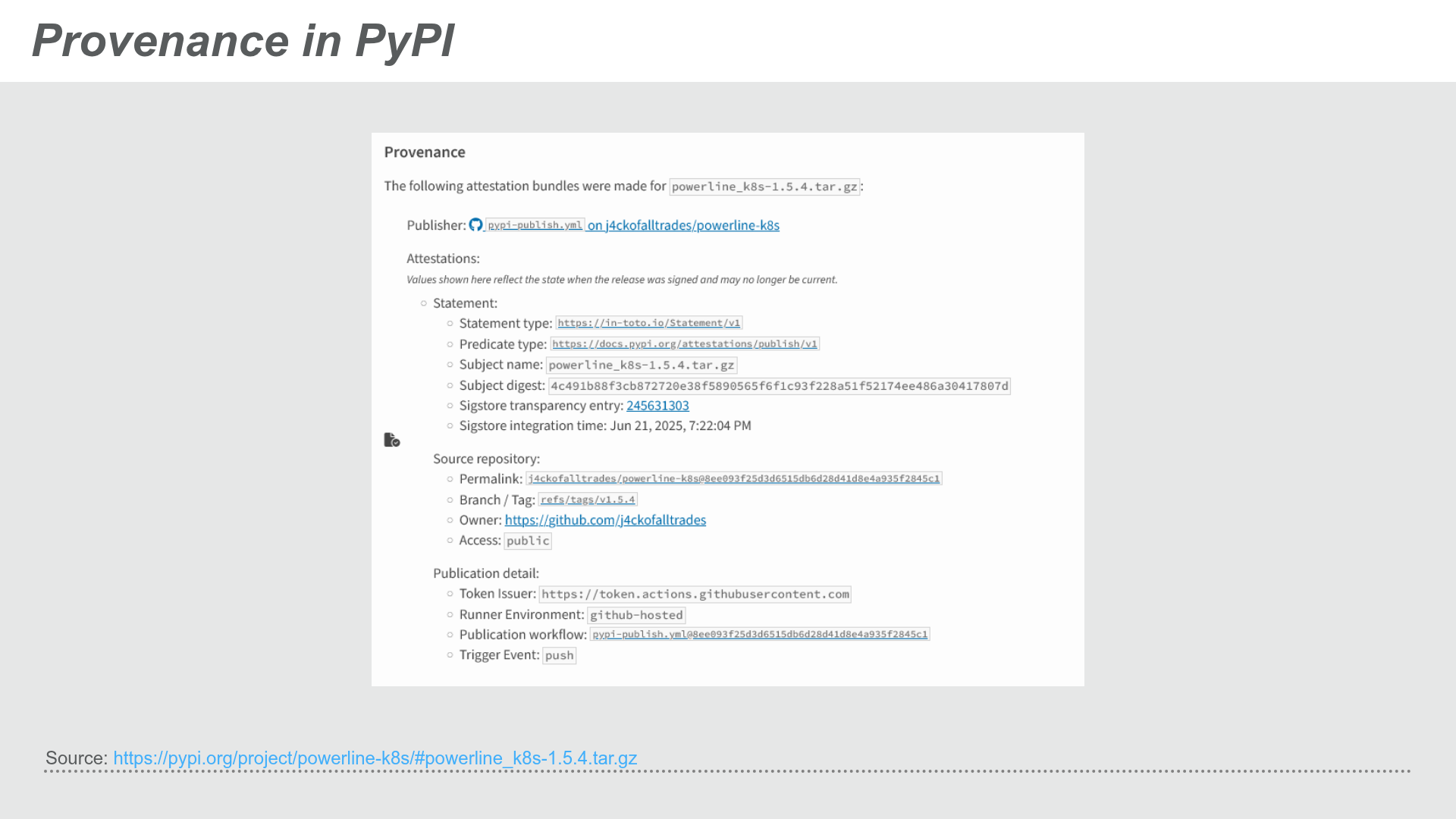
PyPI Provenance UI
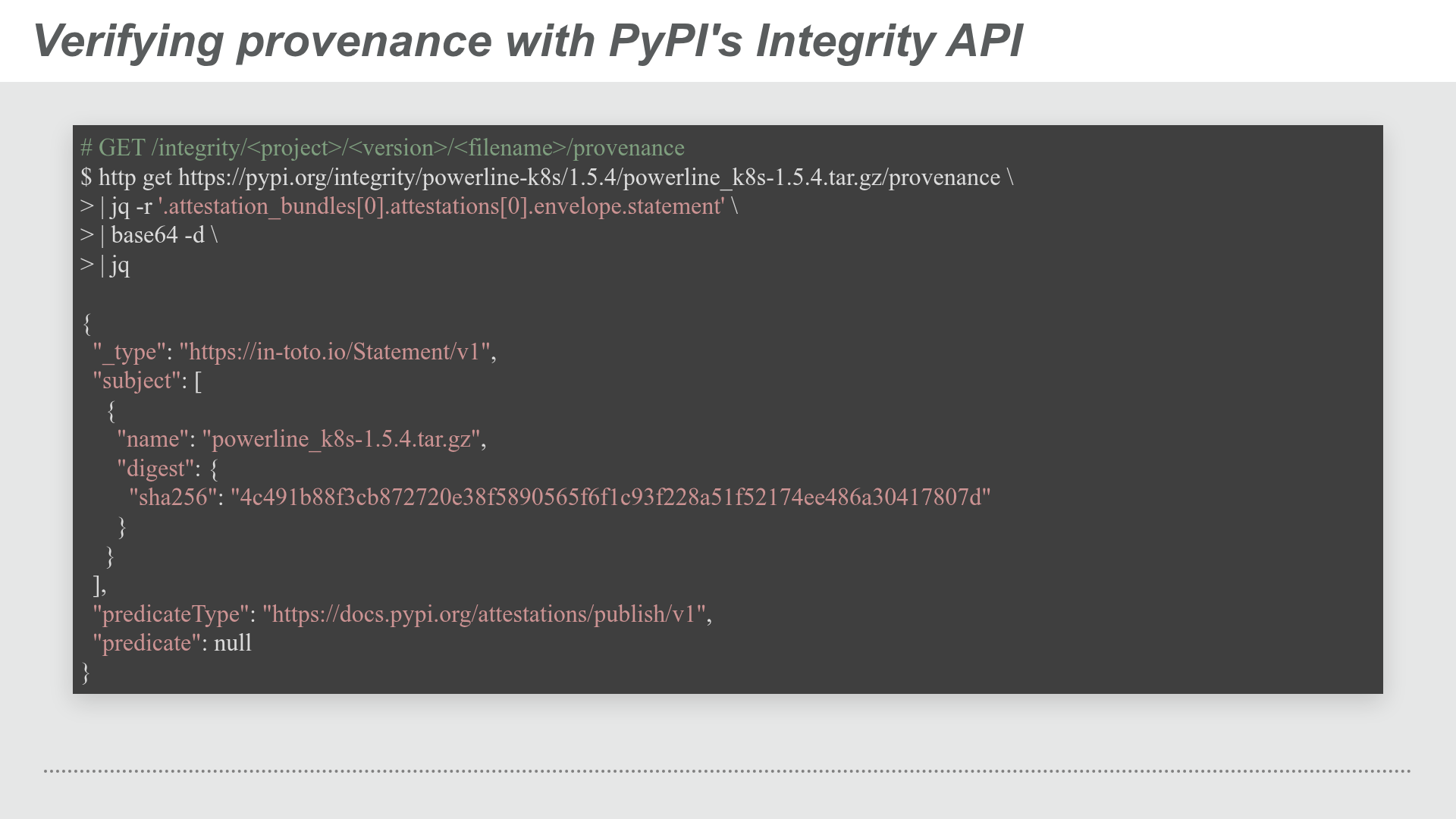
PyPI Integrity API
npm also recently added support for generating provenance statements for packages published to its registry.
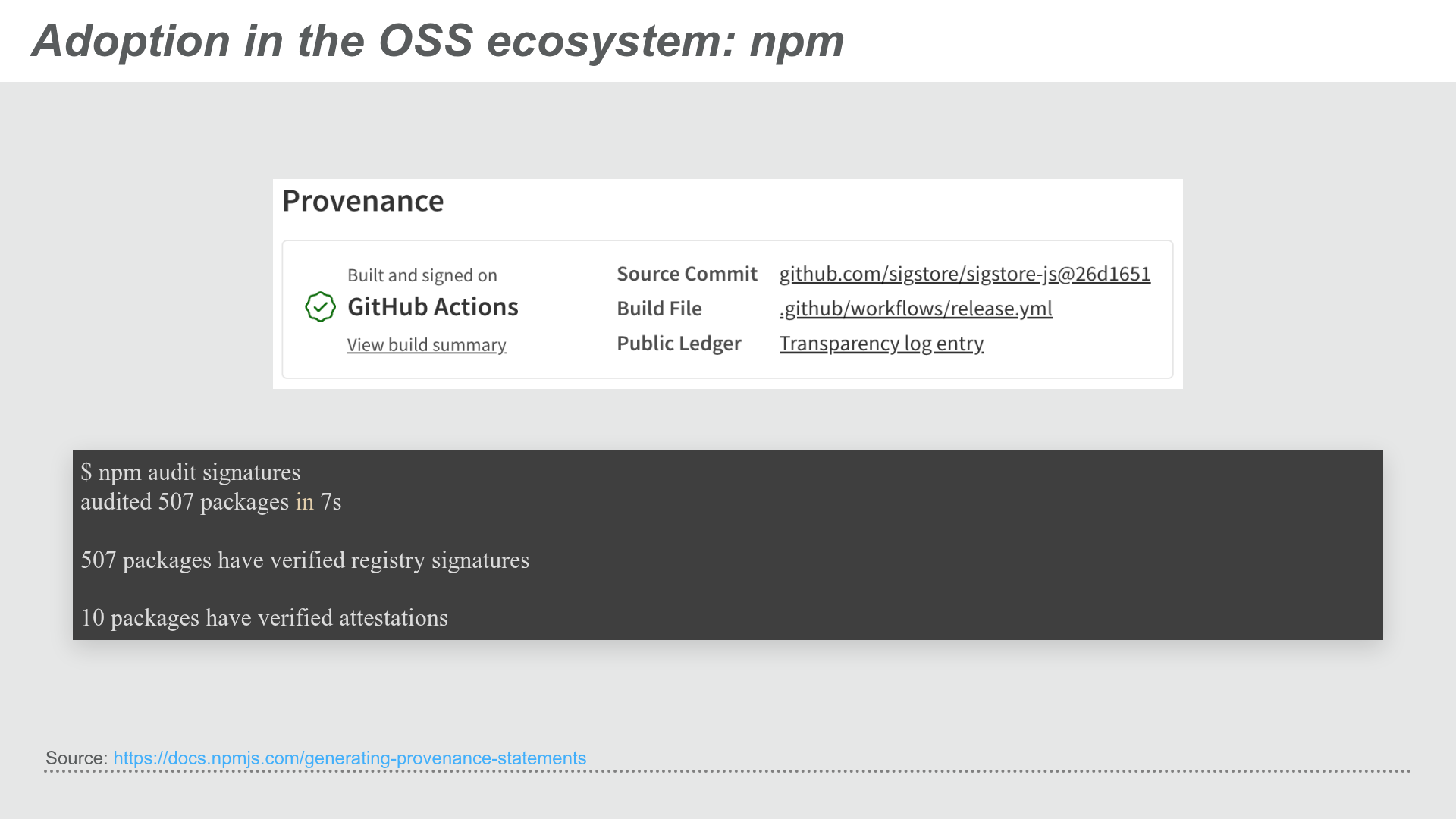
npm support for generative provenance statements
In summary, these security features increase trust in the software supply chain by replacing long-lived API tokens with short-lived OIDC tokens from trusted providers and including cryptographically signed and verifiable signatures with packages when publishing to software registries.
The ideal state is getting to a point where verification of signatures is integrated with tooling like uv and pip. Lastly, these features are not a panacea – they are important steps that we can use to improve overall software supply chain security.
Takeaways